Problem
One of the key challenges for IoT solution providers is to develop an efficient remote software update method for hundreds of thousands of battery-powered devices deployed around the world. Efento has solved this problem by implementing Efento Smart Updates in its devices.
The essence of this solution is securely transmitting only the newly-modified sections of source code to the devices.
Classic method
Many IoT solution providers allow you to remotely transfer a new version of the software to devices already deployed in the field. However, the classic Over the Air (OTA) update is very troublesome, with millions of battery-powered sensors based on cellular networks (NB-IoT and LTE-M). The amount of data transmitted can not only cause destabilization of the network but also seriously burden those devices that are optimized for short transmission sessions.
Efento Smart Updates
To solve these problems, Efento has developed Efento Smart Updates – a software update system for IoT devices based on sending only the changes in software to the already-deployed devices.
This update method has many advantages over the classic OTA updates, including:
- the amount of data transmitted to the device is several times reduced compared to the classic OTA update
- network load is minimized
- longer battery life is ensured in devices
- the measuring system is not destabilized by the lack of measurements during the long update process
Importantly, the software transmission to IoT devices is encrypted. Thanks to server authentication and verification mechanisms of sent data, the software update is completely secure.
How do Efento Smart Updates work?
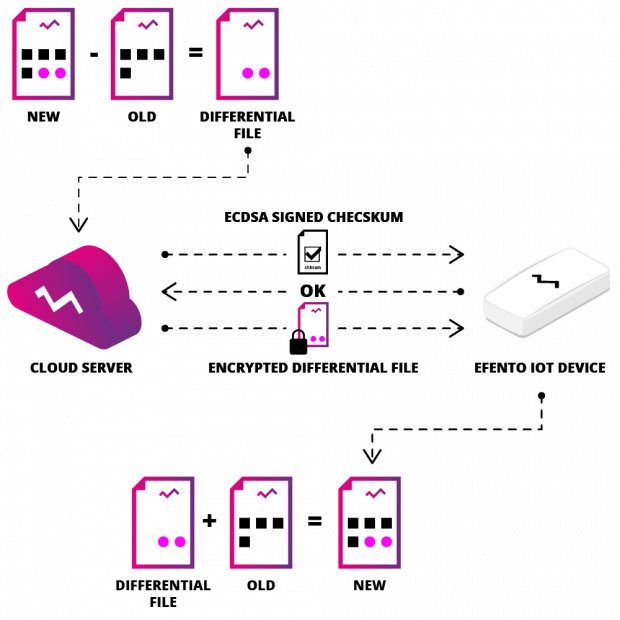
- After completing the work on the new version of the software, we prepare a differential file that is the difference between the new and current versions of the software.
- The differential file is sent to the cloud server and IoT devices are notified of the available update.
- The devices connect to the server and the connection parties negotiate the key that will be used to encrypt communication. The server sends an encrypted update checksum signed according to the ECDSA algorithm. Based on the signature, the IoT device verifies the authenticity of the update.
- The encrypted transmission of updates to the device takes place.
- After the data transmission is completed, the device builds a new software version consisting of the current version and a differential file, after which it calculates the updated checksum.
- If the checksum calculated by the device matches the checksum sent by the server, the software is updated.
